FREE QUIZ
Can you spot the scams? See how you score.
Screen detects scams, fraud, and social engineering attempts, warning you in real time
Partnered institutions to embed SOPs and protect users
Unsure if you're
safe
?
The easiest way to get 24/7 protection
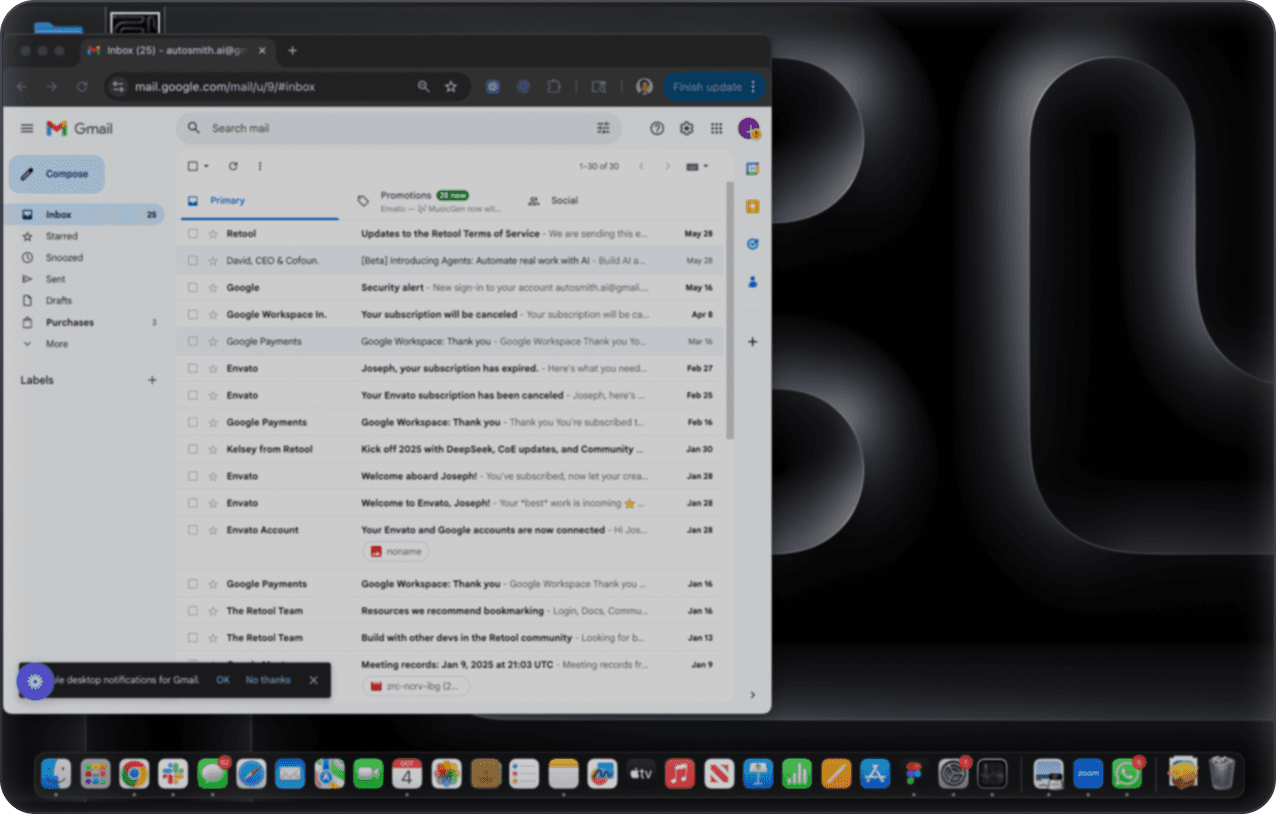
Get real time
protection
We built an AI notification system that stand between you and malicious digital actors, blocking the next risky step so you stay safe on your devices
Proprietary evaluation
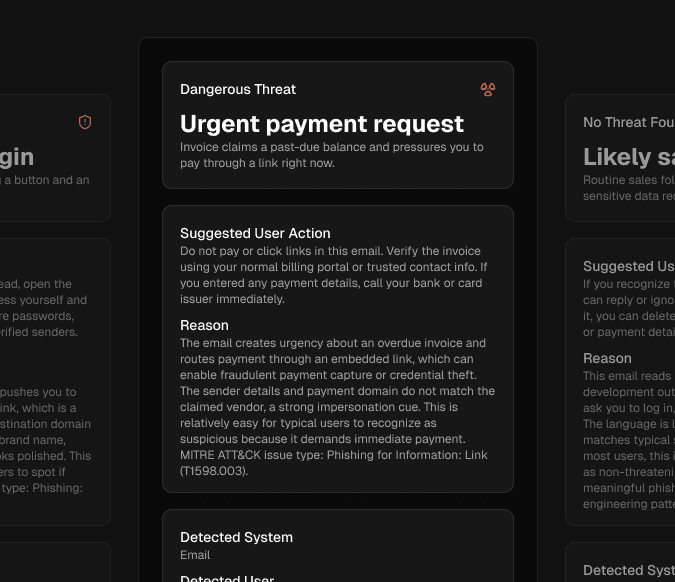
Every check follows a NIST aligned approach, scoring risk based on real scam signals so results stay consistent and explainable
Clear protection & reccomendations
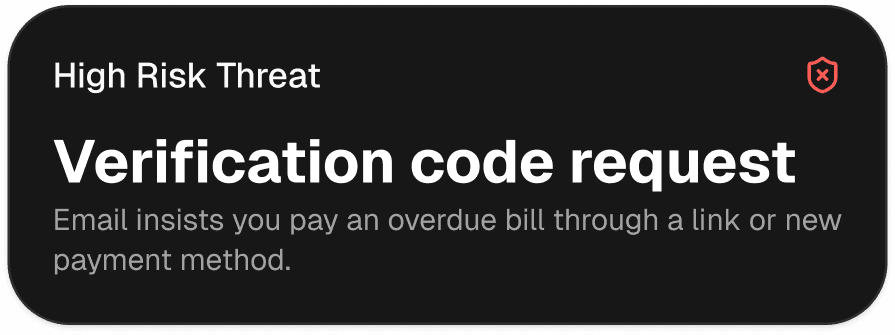
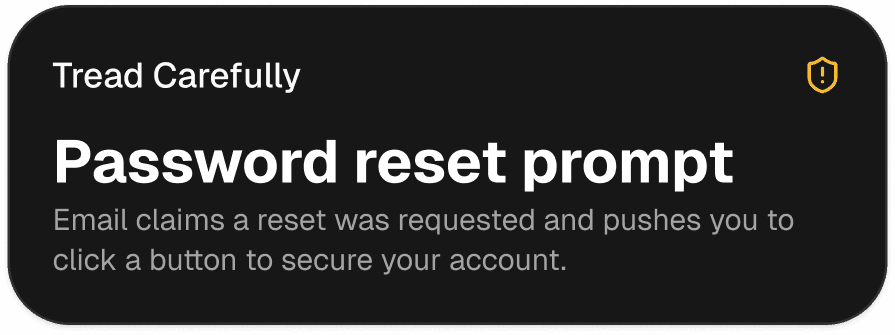
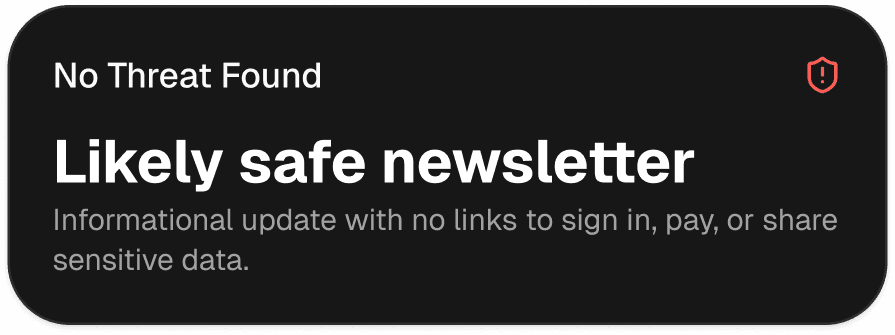
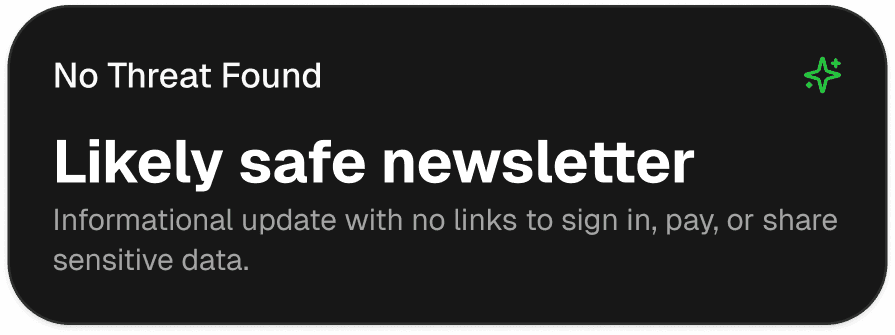
Instant alerts, clear risk labels, and a recommended next step
Fighting AI with AI
Catches subtle scam patterns, including AI generated tricks
Private by design
Actively censors sensitive details during scans
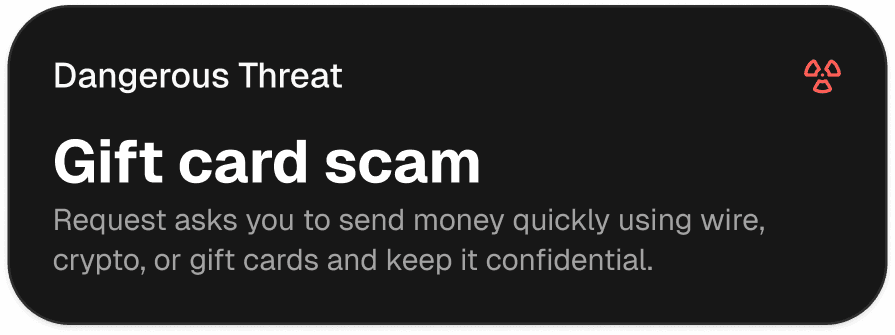
Over 500 scams detected
24
Can you spot the scam?
Most people are more vulnerable than they realize. Take our free 10-minute assessment to uncover your digital blind spots and receive a personalized risk report.
Test your instincts
Review 35 real-world scenarios to see if you can spot a professional trap
Get your scam awarness score
Receive a score and a personalized plan to fix your specific security risks
Frequently asked questions
Get answers to commonly asked questions.
Get early access to Screen
Scan anything you’re unsure about and get a clear risk label and next step in seconds.