Early Access
Get invites as spots open.
Protection against modern AI-driven threats
Protection against modern AI-driven threats
Protection against modern AI-driven threats
We’re building a cybersecurity tool to protect people from scams, fraud, and social engineering attacks in real time.
Systems Active
Device: Mac Desktop, macOS Sierra
General Summary
Safety Log
Search
Risk Exposure This Week
14% Risk Exposure
-3% vs last week
Stopped Threats This Week
36 Stopped this week
+22% vs last week
Threats in the last 30 days
10/01
10/06
10/11
10/16
10/21
10/26
Version: v0.1.3
Activate Screen
Systems Active
Device: Mac Desktop, macOS Sierra
General Summary
Safety Log
Search
Risk Exposure This Week
14% Risk Exposure
-3% vs last week
Stopped Threats This Week
36 Stopped this week
+22% vs last week
Threats in the last 30 days
10/01
10/06
10/11
10/16
10/21
10/26
Version: v0.1.3
Activate Screen
Systems Active
Device: Mac Desktop, macOS Sierra
General Summary
Safety Log
Search
Risk Exposure This Week
14% Risk Exposure
-3% vs last week
Stopped Threats This Week
36 Stopped this week
+22% vs last week
Threats in the last 30 days
10/01
10/06
10/11
10/16
10/21
10/26
Version: v0.1.3
Activate Screen
Systems Active
Device: Mac Desktop, macOS Sierra
Risk Exposure This Week
14% Risk Exposure
-3% vs last week
Stopped Threats This Week
36 Stopped this week
+22% vs last week
Version: v0.1.3
Activate Screen
Systems Active
Device: Mac Desktop, macOS Sierra
Risk Exposure This Week
14% Risk Exposure
-3% vs last week
Stopped Threats This Week
36 Stopped this week
+22% vs last week
Version: v0.1.3
Activate Screen
Partnered institutions to embed SOPs and protect users



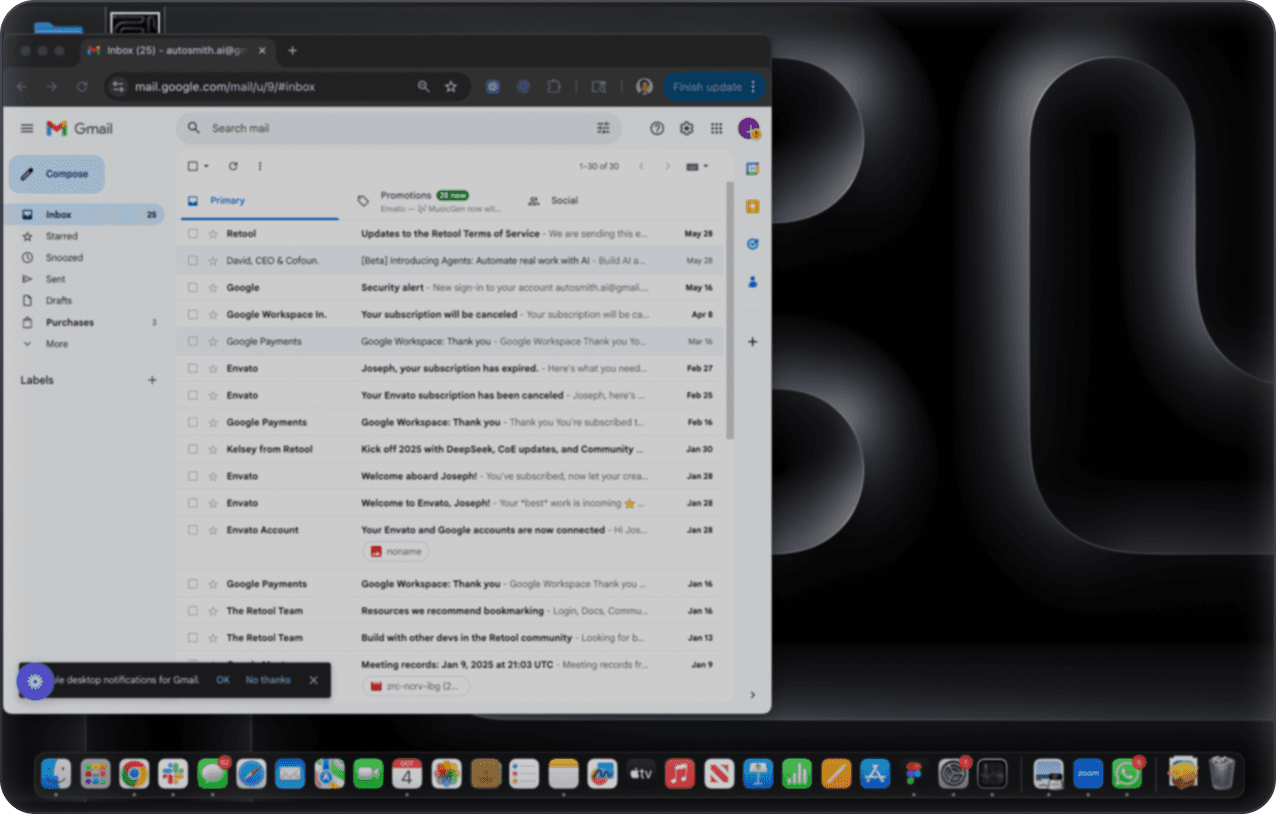
Check safety before you click
Protect yourself using our real-time AI that stand between you and malicious actors, blocking the next risky step so you stay safe on your devices.
Phishing
Scareware

Phishing
Scareware

Phishing
Scareware
The internet is crawling with threats
Scams hide in everyday messages and websites
Real-time protection
Instant alerts, clear risk labels, and a recommended next step.
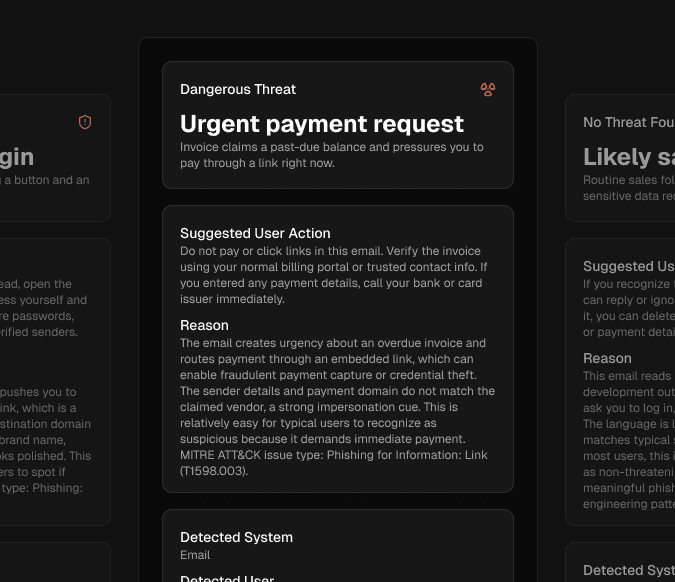


Threat evaluation
We use AI to assess risk against documented attacker tactics and trusted signals, then returns a clear next step in seconds.
AI is accelerating this problem
Generative AI makes scams faster and easier to scale
Clarity
in seconds
When something feels off, run a quick scan and get a clear result, plus the safest next move.

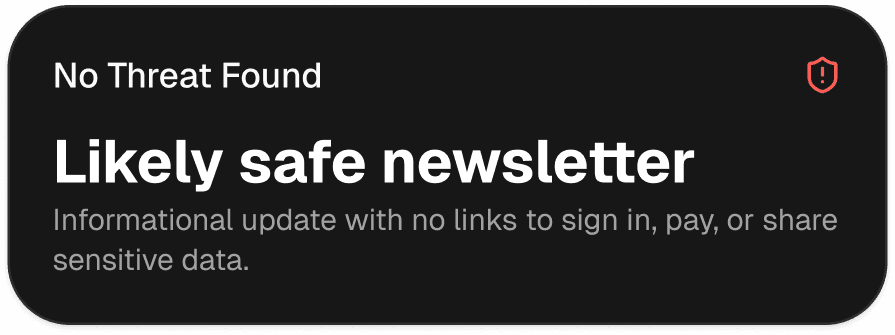




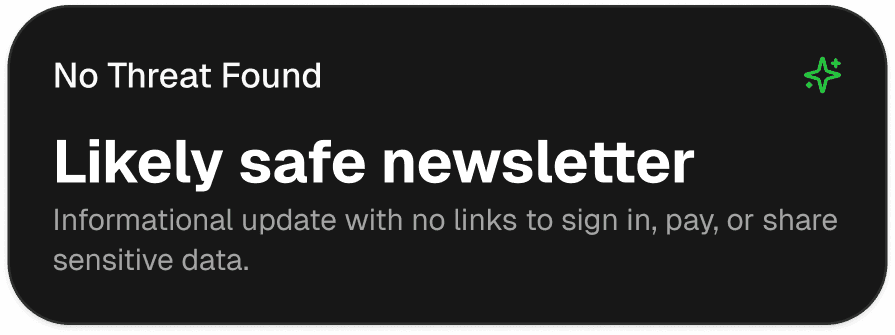

Scan Page
Scan Page


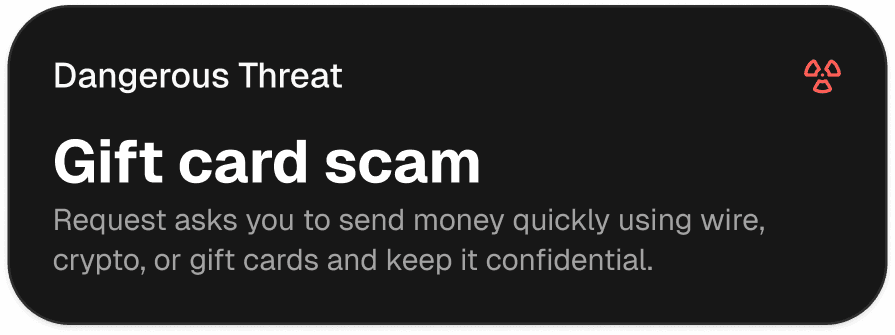

Scan anything
Analyze messages, links, login screens, and pop-ups in seconds across email, web, SMS, and chat.
Scan anything
Analyze messages, links, login screens, and pop-ups in seconds across email, web, SMS, and chat.
Scan anything
Analyze messages, links, login screens, and pop-ups in seconds across email, web, SMS, and chat.
Clear risk score
Grade risk using NIST-aligned phishing guidance, with signals that explain why it was flagged.
Clear risk score
Grade risk using NIST-aligned phishing guidance, with signals that explain why it was flagged.
Clear risk score
Grade risk using NIST-aligned phishing guidance, with signals that explain why it was flagged.
Knows scam patterns
Match indicators to a tactics knowledge base, grounded in real-world observations and reports.
Knows scam patterns
Match indicators to a tactics knowledge base, grounded in real-world observations and reports.
Knows scam patterns
Match indicators to a tactics knowledge base, grounded in real-world observations and reports.
Works across devices
Deliver decisions on desktop and mobile, so protections follow you wherever you work online.
Works across devices
Deliver decisions on desktop and mobile, so protections follow you wherever you work online.
Works across devices
Deliver decisions on desktop and mobile, so protections follow you wherever you work online.
What we protect against
24
threat types documented and adding more every month
integrations and growing
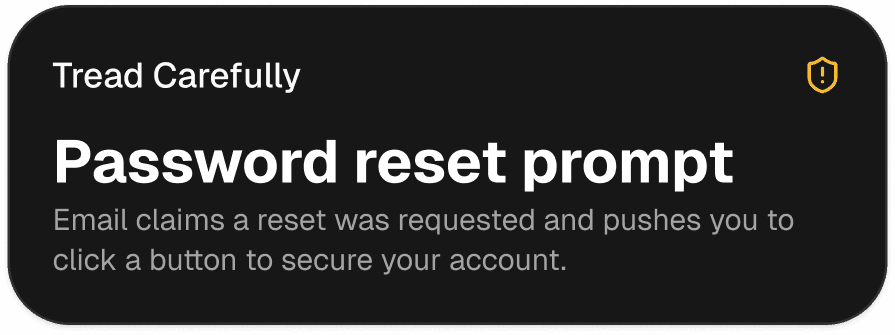
Phishing and fake logins
Flag login traps, spoofed senders, and sketchy links early
Spear Phishing Link
Fake Login Page
Lookalike Domain
QR Phishing
URL Shorteners
OAuth Consent Trap
6
Phishing and fake logins
Flag login traps, spoofed senders, and sketchy links early
Spear Phishing Link
Fake Login Page
Lookalike Domain
QR Phishing
URL Shorteners
OAuth Consent Trap
6
Phishing and fake logins
Flag login traps, spoofed senders, and sketchy links early
Spear Phishing Link
Fake Login Page
Lookalike Domain
QR Phishing
URL Shorteners
OAuth Consent Trap
6
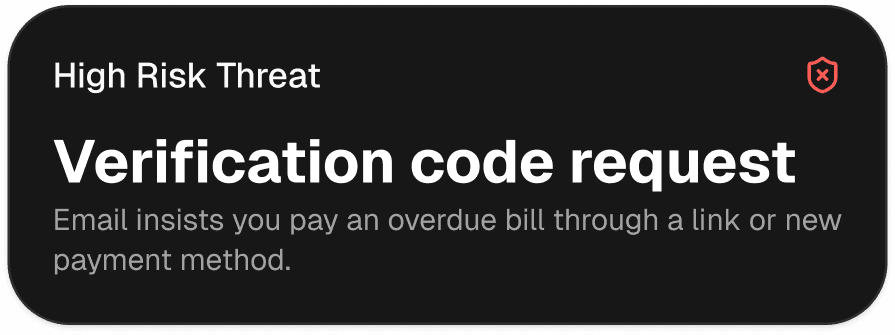
Payments and billing scams
Catch invoice tricks and payment reroutes in real time now
Urgent Payment Request
Wire Reroute
Gift Card Scam
Fake Receipt
Subscription Charge Trap
Refund Scam
6
Payments and billing scams
Catch invoice tricks and payment reroutes in real time now
Urgent Payment Request
Wire Reroute
Gift Card Scam
Fake Receipt
Subscription Charge Trap
Refund Scam
6
Payments and billing scams
Catch invoice tricks and payment reroutes in real time now
Urgent Payment Request
Wire Reroute
Gift Card Scam
Fake Receipt
Subscription Charge Trap
Refund Scam
6



Impersonation and pressure
Spot imposters and high-pressure asks before you act online
Boss Impersonation
Bank Impersonation
IT Support Spoof,
Vendor Spoof,
Account Shutdown Threats
5
Impersonation and pressure
Spot imposters and high-pressure asks before you act online
Boss Impersonation
Bank Impersonation
IT Support Spoof,
Vendor Spoof,
Account Shutdown Threats
5
Impersonation and pressure
Spot imposters and high-pressure asks before you act online
Boss Impersonation
Bank Impersonation
IT Support Spoof,
Vendor Spoof,
Account Shutdown Threats
5
Risky sites and shady sellers
Assess unknown sites using public reviews and registry data
Bad Reviews Pattern
BBB Complaints
Chargeback Reports
No Contact Info
Missing Refund Terms
Domain Age
6
Risky sites and shady sellers
Assess unknown sites using public reviews and registry data
Bad Reviews Pattern
BBB Complaints
Chargeback Reports
No Contact Info
Missing Refund Terms
Domain Age
6
Risky sites and shady sellers
Assess unknown sites using public reviews and registry data
Bad Reviews Pattern
BBB Complaints
Chargeback Reports
No Contact Info
Missing Refund Terms
Domain Age
6
Upgrade your digital protection
Early access includes full features for free while we test and improve the system
Starter
Free
5 scans / month
Limited threat check
Limited trusted SOP check
Limited AI context grading
Basic
$
10
per month
Billed yearly
Unlimited scans
Unlimited threat check
Unlimited trusted SOP check
Unlimited AI context grading
Pro
Recommended
$
25
per month
Billed yearly
Everything in Basic, plus:
Multi device protection
24/7 automated protection
Behavior learning AI
Priority support
Enterprise
Custom
Everything in Pro, plus:
Admin controls & reporting
Role-based permissions
Local network hosting
Integrate insustry procedural templates
Starter
Free
5 scans / month
Limited threat check
Limited trusted SOP check
Limited AI context grading
Basic
$
10
per month
Billed yearly
Unlimited scans
Unlimited threat check
Unlimited trusted SOP check
Unlimited AI context grading
Pro
Recommended
$
25
per month
Billed yearly
Everything in Basic, plus:
Multi device protection
24/7 automated protection
Behavior learning AI
Priority support
Enterprise
Custom
Everything in Pro, plus:
Admin controls & reporting
Role-based permissions
Local network hosting
Integrate insustry procedural templates
Starter
Free
5 scans / month
Limited threat check
Limited trusted SOP check
Limited AI context grading
Basic
$
10
per month
Billed yearly
Unlimited scans
Unlimited threat check
Unlimited trusted SOP check
Unlimited AI context grading
Pro
Recommended
$
25
per month
Billed yearly
Everything in Basic, plus:
Multi device protection
24/7 automated protection
Behavior learning AI
Priority support
Enterprise
Custom
Everything in Pro, plus:
Admin controls & reporting
Role-based permissions
Local network hosting
Integrate insustry procedural templates
Frequently asked questions
Get answers to commonly asked questions.
What does early access mean?
You get first access to new features while everything is being tested and improved, and your feedback helps shape what ships next. We’ll reach out directly when spots open so you can join.
Does it work across devices?
Yes. Protection follows you across desktop and mobile so you get consistent results wherever you are.
What can I scan?
Anything you see on your screen, including messages, links, login pages, and pop-ups.
How does it decide what’s risky?
It matches what you’re seeing to documented attacker tactics and trusted signals, then returns a clear risk label and recommended next step.
Is my data private?
Yes. Content is automatically censored before analysis, and only the minimum signals needed are used to produce a decision.
What does early access mean?
You get first access to new features while everything is being tested and improved, and your feedback helps shape what ships next. We’ll reach out directly when spots open so you can join.
Does it work across devices?
Yes. Protection follows you across desktop and mobile so you get consistent results wherever you are.
What can I scan?
Anything you see on your screen, including messages, links, login pages, and pop-ups.
How does it decide what’s risky?
It matches what you’re seeing to documented attacker tactics and trusted signals, then returns a clear risk label and recommended next step.
Is my data private?
Yes. Content is automatically censored before analysis, and only the minimum signals needed are used to produce a decision.
What does early access mean?
You get first access to new features while everything is being tested and improved, and your feedback helps shape what ships next. We’ll reach out directly when spots open so you can join.
Does it work across devices?
Yes. Protection follows you across desktop and mobile so you get consistent results wherever you are.
What can I scan?
Anything you see on your screen, including messages, links, login pages, and pop-ups.
How does it decide what’s risky?
It matches what you’re seeing to documented attacker tactics and trusted signals, then returns a clear risk label and recommended next step.
Is my data private?
Yes. Content is automatically censored before analysis, and only the minimum signals needed are used to produce a decision.


Get early access to Screen
Scan anything you’re unsure about and get a clear risk label and next step in seconds.